
University of Saskatchewan
Computer Security Research Lab
Research
The lab research activities are motivated by the interests towards practical solutions to security problems faced by industry and understanding of basic problems in security. Throughout the years of R&D research and work with industry the lab has developed and adopted an integrated research and education program that is centered on the practical security. Through these R&D activities, all our students are involved in a hands-on, experiential research. The special focus of our program is code attribution, software security, malware analysis and IoT security.
Code Attribution

Code authorship attribution is the process of identifying the author of a given code. With increasing numbers of malware and advanced mutation techniques, the authors of malware are creating a large number of malware variants. To better deal with this problem, methods for examining the authorship of malicious code are necessary. Code authorship attribution techniques can thus be utilized to identify and categorize the authors of malware.
Software protection: reverse engineering & obfuscation
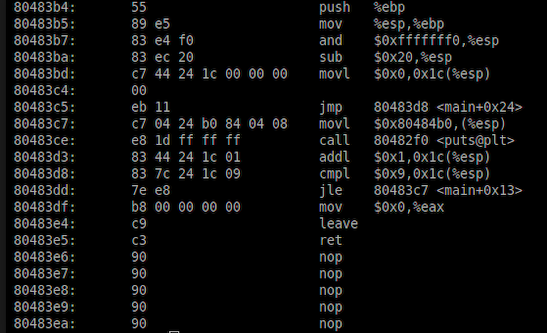
The goal of code obfuscation is to modify original software using semantics-preserving transformations to disguise its appearance, intent, and to protect it from reverse engineering (process of deconstructing code into components to understand its inner workings) and avoid detection techniques. In an adversarial context, obfuscation helps to create transient and evasive malware. As the underground community is constantly developing and evolving new complex tools to avoid detection, understanding, and recognizing what type of obfuscation is being used is critical in software protection.
Malware analysis

Everything changes when a threat of malware attack becomes your number one priority. Recent cyberattacks have caused severe consequences in critical sectors including healthcare, the financial industry, and national defense. Malicious software, or malware, has become an ultimate tool in these attacks.
E-health security

Medical devices have been and remain vulnerable to cyberattacks due to naïve designs and weak security implementations. There have not yet been any reports of death or injuries from maliciously compromised medical devices, but there are many examples of patient injuries or personal information leaks due to security vulnerabilities and a lack of security controls in medical devices